
Nothing strikes fear quite like a cyber attack this days. One of the most intimidating is the Distributed Denial-of-Service (DDoS) attack—a deliberate overload of your website or server that can bring your entire operation grinding to a halt. At telaHosting, we’ve seen the chaos it can cause: empty shopping carts, lost transactions, frustrated users, and a tarnished reputation.
But there’s a powerful way to fight back using the same system that connects your domain to the world: DNS (Domain Name System). In this blog, we’ll explore what a DDoS attack looks like, why it’s so effective, and most importantly—how DNS solutions, combined with smart strategies, can help prevent or mitigate its impact. By understanding this and preparing your infrastructure, you’re not just defending your digital storefront—you’re safeguarding your brand’s future.
What is a DDoS Attack?
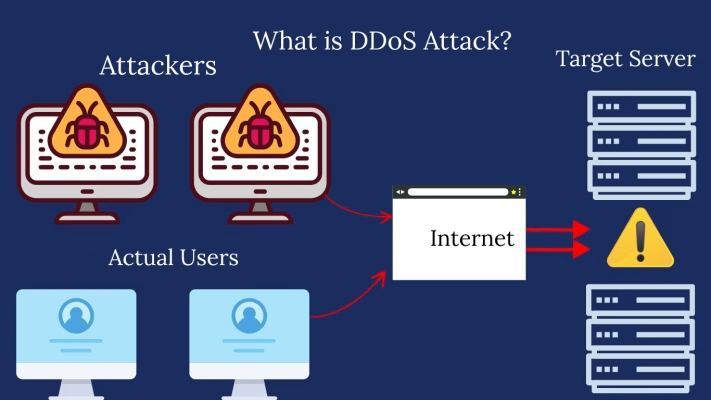
A Distributed Denial-of-Service (DDoS) attack is a coordinated cyberattack where hackers use multiple internet-connected devices—often numbering in the thousands or even millions, to flood a target system with traffic. The goal? Not to break in, not to steal data, but to completely exhaust your online services, so that genuine users, customers, or employees can no longer access them.
Let me put it this way, imagine you own a store. It’s a busy day, and suddenly a massive crowd of people shows up. But none of them are there to shop. They’re just standing around, clogging the entrance, asking nonsense questions, or wandering aimlessly. They take up space, overwhelm your staff, and push out the actual paying customers. That’s exactly what a DDoS attack feels like—a digital stampede with zero buying intentions.
What makes DDoS attacks even more frustrating is that they’re hard to stop once they start. Unlike a single hacker breaking in through a side door, a DDoS comes at you from every direction. It’s like trying to swat flies during a hurricane.
And in today’s world where everything from online stores to banking systems and public services runs on the internet, the impact of such an attack? Massive. Downtime means lost revenue, broken trust, and potential long-term damage to your brand.
How Does a DDoS Attack Work?
So, how do these attacks actually play out? Let’s walk through the chaos step by step, and you’ll see how something so technical can create very real-world problems.
Step 1: Building the Botnet Army
It all starts with hackers secretly infecting internet-connected devices with malicious software. These aren’t just computers—they can be smartphones, routers, CCTV cameras, smart fridges, even your voice assistant. Yes, your Alexa might unknowingly be part of a cyberattack!
This zombie-like network of infected devices is called a botnet. And just like zombies in movies, they don’t act on their own. They’re controlled remotely by the attacker.
Now imagine the attacker has control of 10,000 or 100,000 devices. That’s not just a headache—it’s a full-blown migraine waiting to happen.
Step 2: Launching the Attack
Once the botnet is ready, the hacker gives the command: “Attack that target.”
And boom—every device in the botnet starts flooding your server with data. It could be fake requests to load your homepage, open multiple apps, ping your login page, or download files—all at the same time.
If your server is built to handle 500 visitors a minute, and suddenly 10,000 bots are knocking every second, guess what? Your server gets confused, overloaded, and eventually just… gives up.
Step 3: Overload and Disruption
Your site now starts lagging, pages take forever to load (if they load at all), and users begin to drop off. For them, it feels like the site is broken. They might even assume your business has shut down or that it’s been hacked.
Meanwhile, your internal team might lose access to tools and dashboards, your email system could stop functioning, and if you’re running an online shop, sales grind to a halt.
The attacker doesn’t need to breach your security, steal passwords, or touch your databases. They just need to clog the digital pipes until everything comes to a stop.
Step 4: Damage Without Data Theft
No files are stolen, no security walls are breached, and yet the damage is staggering. It’s like someone locking your office from the outside. They don’t need to take anything—they just stop business from happening.
The fallout?
- Lost revenue (especially if you’re an e-commerce site)
- Frustrated customers
- Damaged reputation
- Security concerns from stakeholders and users
Some hackers even follow this up with a ransom demand: “Pay us to stop the attack.” And that’s where DDoS turns from a nuisance into full-blown extortion.
Why Are DDoS Attacks So Devastating?
DDoS attacks are so dangerous because they don’t need to “hack” your systems to take them down. They weaponize traffic—and for many Nigerian businesses with limited infrastructure, that’s more than enough to cause serious trouble.
Let’s break down the impact:
-
Volume Overload
A sudden spike of malicious traffic exhausts your server’s bandwidth or overwhelms your firewall. Just like a traffic jam, everything grinds to a halt. Your website becomes slow—or completely unresponsive.
-
Application Layer Targeting
Some DDoS attacks are stealthier. Instead of just sending random traffic, they mimic real user behavior—loading web pages, filling forms, or triggering APIs. These are harder to detect and can silently choke your resources, eating up CPU and memory until your app crashes.
-
Shortage of Resources
Let’s face it—most Nigerian startups and SMEs don’t have access to huge cloud servers or global load-balancing tools. That makes them easy prey. A single, well-coordinated DDoS attack can knock your operations offline for hours or even days.
-
Collateral Damage
When your site or email goes down, it doesn’t just affect your tech—it affects your customers’ trust. Imagine running a promo or launching a new service, only for your platform to go dark. Lost sales, bad reviews, and customer doubt follow quickly.
-
Compliance & Legal Risks
If your business operates in regulated sectors—like fintech, healthcare, or education—downtime can trigger compliance violations. You may face data exposure concerns, failed service-level agreements (SLAs), and even regulatory fines.
Real-World Relevance in Nigeria
Nigeria’s digital economy is booming—but with growth comes risk. From Lagos to Abuja, we’re seeing more businesses moving online, handling payments, processing customer data, and hosting services on public infrastructure. This visibility makes them prime targets for cybercriminals.
And the worst part? DDoS attacks are cheap to launch. On the dark web, anyone with a few dollars can hire a botnet to bombard your domain for hours. That means your competitor, a disgruntled ex-employee, or a cybercriminal halfway across the world could initiate an attack within minutes.
A DDoS attack isn’t just a technical problem—it’s a business threat that can damage everything you’ve worked hard to build.
How DNS Plays a Role in Preventing DDoS Attacks
The Domain Name System is often the first line of defense. When used strategically, DNS can:
- Absorb DDoS traffic across multiple servers
- Detect anomalies in traffic patterns early
- Redirect or block traffic before it reaches your infrastructure
Let’s explain further:
-
Traffic Load Distribution: Anycast & Geo-Load Balancing
Anycast DNS Routing
Imagine a Lagos-based online store receiving thousands of requests per second, not just from customers, but also from attackers trying to overwhelm your site. Without protection, all those requests slam into one server—and it crashes. That’s where Anycast DNS routing comes in.
With Anycast, your DNS doesn’t route traffic to just one location. Instead, it directs each incoming request to the closest, fastest, or most available server in your global network. Think of it like ride-hailing apps: your request goes to the nearest driver, not the first one available across town.
This setup means:
- DDoS traffic is dispersed, not concentrated on one server.
- If one location is overwhelmed, others take over—no downtime.
- Users experience faster load times because they’re connected to the nearest server.
Geo-Load Balancing
Geo-load balancing allows you to route, restrict, or limit traffic based on its country, region, or network source. If your business mainly serves Nigerian customers, and you suddenly get a flood of traffic from Eastern Europe, something’s off.
With geo-based DNS policies, you can:
- Thwart suspicious spikes by automatically blocking or throttling high-risk regions.
- Redirect traffic to safer servers or to an “under maintenance” page when anomalies are detected.
- Isolate test campaigns, A/B pages, or backups to only certain areas.
This is crucial for local businesses in Nigeria that might be under-targeted by international botnets. telaHosting’s DNS solution gives you control over where your traffic goes, and what happens if it starts behaving badly.
-
Early Detection and Threat Blocking
DNS Anomaly Scanning
In the world of cybersecurity, early detection is everything. Modern DNS infrastructure isn’t just reactive—it’s proactively watching every request that comes in. This is where anomaly scanning steps in.
Here’s how it works:
- Your DNS service learns your normal traffic patterns—volume, source, timing.
- When it sees a sudden surge, especially from unknown or flagged sources, it raises a red flag.
- It can then automatically rate-limit or block those suspicious requests until reviewed.
For example, if your site usually gets 300 DNS queries per minute and it suddenly spikes to 20,000—our system at telaHosting knows this isn’t business as usual. We instantly step in to block the threat, reducing damage before your users even notice.
Challenge-Response Verification
Not all DDoS traffic is easy to spot. Some bots try to act like real users, sending requests that mimic typical browsing behavior. That’s why DNS now includes challenge-response verification which is a clever technique similar to CAPTCHA.
Here’s what happens:
- A DNS resolver suspects a bot is making too many or unusual requests.
- It sends back a digital challenge that only a legitimate browser or device can solve.
- If the source doesn’t respond correctly (as most bots can’t), it gets blocked instantly.
This process helps screen out malicious traffic without interrupting service for real users. At telaHosting, we’ve embedded these security layers into our DNS firewall, so bots get stopped, while your Nigerian customers browse safely and without delay.
-
Intelligent Traffic Rerouting and Scrubbing
Black/Graylisting
Think of a DDoS attacker like a known troublemaker trying to crash your party. With blacklisting, you put them on the “do not enter” list. DNS-level black/graylisting filters known bad IPs and suspicious sources before they even get near your web servers.
What makes it powerful:
- Lists update dynamically in real time based on global threat databases.
- DNS responds with “no route” or null answers to known bad actors.
- You stay safe and visible to real users—without blocking legitimate traffic.
Even better? telaHosting’s DNS system integrates with global cybersecurity feeds and our internal threat database. If an IP address attacks one of our clients, it’s flagged across our network—protecting everyone.
Traffic Scrubbing
Not all DDoS traffic looks dirty. Some requests can slip past filters by mimicking real users. That’s where scrubbing comes in—think of it as a security checkpoint that inspects, cleans, and verifies every request before it hits your server.
Here’s how it works:
- Suspicious traffic is redirected to a scrubbing center.
- There, algorithms analyze patterns, headers, and behaviors.
- Valid requests are allowed through. Malicious ones get discarded.
At telaHosting, we offer integrated traffic scrubbing as part of our hosting packages—especially for mission-critical platforms like Nigerian fintech startups, online retailers, and public institutions. You get big-enterprise protection, minus the big-enterprise budget.
Best-Practices to Reinforce DNS Layer DDoS Defenses
1. Use Rate Limiting on Authoritative Servers
Rate limiting is like having a smart security guard at your server door—one who lets in genuine visitors but blocks anyone trying to rush the gates. When implemented on authoritative DNS servers, rate limiting restricts how many queries a single IP address can send per second or minute.
This is especially helpful during DDoS attacks because:
- Attackers flood your DNS with repeated requests—rate limiting filters out these excesses.
- Legitimate users don’t get affected, as their query volume stays normal.
- It protects server resources, ensuring uptime and availability even under load.
Real-World Example
If an attacker-controlled botnet sends 10,000 fake DNS lookups per minute, rate limiting can cut off that stream after 50 or 100 requests, instantly easing the pressure on your infrastructure.
At telaHosting we automatically apply DNS-level rate limits during high-traffic anomalies. For clients expecting legitimate spikes—like flash sales or webinars—we customize thresholds to balance protection and performance.
2. Increase DNS Cache Lifetimes (TTL Optimization)
TTL (Time to Live) controls how long a DNS record is stored (cached) before it needs to be fetched again. A longer TTL means fewer DNS requests, which lightens the load on your DNS servers during potential DDoS spikes.
Think of it like this: If everyone knows the directions to your house, you don’t need to answer the door 1,000 times an hour. Caching directions (via TTL) keeps traffic flowing smoothly.
Why It Helps Against DDoS
- Reduces DNS query frequency—critical during high-load periods.
- Keeps your domain resolving even if your authoritative server is struggling.
- Protects users from propagation delays during record changes.
Best Practice
- Set longer TTL (e.g., 1–24 hours) for static records like your A or CNAME.
- Use shorter TTL (5–15 mins) for records that change often, like MX or temporary redirects.
At telaHosting, our DNS dashboard makes TTL adjustments easy, and our support team helps recommend values tailored to your business needs and attack posture.
3. Enable DNSSEC for Record Integrity
DNSSEC (Domain Name System Security Extensions) is like sealing your DNS records with a digital stamp. It ensures that when a user queries your domain, they receive a response that hasn’t been altered, forged, or spoofed.
While DNSSEC doesn’t block traffic floods, it prevents cache poisoning attacks, which are sometimes used alongside DDoS to redirect users to malicious sites.
Why It Matters
- Validates the authenticity of your DNS data.
- Prevents attackers from modifying DNS responses and tricking users.
- Helps reinforce public trust, especially for e-commerce, finance, and health platforms.
How It Works
- Your DNS records are signed with private cryptographic keys.
- DNS resolvers check this signature using public keys before delivering results.
- If the validation fails, users won’t be sent to fake or compromised servers.
At telaHosting, DNSSEC is offered as a one-click setup with every domain registration. We also manage key rotation and DS record submission—making it effortless for you.
4. Engage a Backup DNS or CDN Provider
Even with the best infrastructure, outages can happen. That’s why secondary DNS or Content Delivery Networks (CDNs) exist—to act as an emergency escape plan.
Backup DNS Benefits
- Provides failover capability if your primary DNS goes down.
- Synchronizes your DNS zone data in real-time, ensuring continuity.
- Ensures your domain still resolves, even if you’re under direct attack.
CDN Benefits
- Caches your website content across global edge servers.
- Absorbs traffic surges with high redundancy.
- Adds layers of security, like web firewalls and bot filters.
At telaHosting, we offer direct integrations with trusted CDN partners and backup DNS providers. We can help you set up dual-layer DNS so your domain stays live—even when things go south.
5. Regular DDoS Simulations and DNS Health Monitoring
Being proactive beats being reactive. That’s why smart businesses periodically simulate DDoS attacks or run DNS stress tests to see how their infrastructure holds up.
DNS health monitoring tools like: DNS checker, MXtoolbox, IntoDns etc.
- Continuously scan for anomalies, downtime, or slow resolution.
- Alert you in real-time when performance dips.
- Help you fine-tune your DNS settings for maximum uptime.
DDoS Simulation Benefits
- Identify weak points in your DNS and server layers.
- Test how well your rate limiting, blacklists, or DNSSEC respond under pressure.
- Improve response time and training for your IT/security team.
At telaHosting, we provide DNS uptime reports and offer periodic simulations for clients who want to ensure their DNS is ready for anything—especially mission-critical businesses in fintech, education, and e-commerce.
Why You Should Prioritize DNS for DDoS Prevention
-
Cost-Effective Scalability
Most small and medium-sized businesses in Nigeria don’t have the luxury of spending millions on cybersecurity. Fortunately, you don’t need expensive hardware or enterprise firewalls to defend yourself from DDoS attacks. A well-configured DNS system can do wonders.
Instead of absorbing all the attack traffic on your main server:
- DNS distributes the load across multiple locations.
- It screens and filters suspicious queries before they reach your infrastructure.
- And it can scale naturally as your traffic grows—without costly software or hardware upgrades.
At telaHosting, our DNS solution is designed to be affordable yet powerful—giving startups, SMEs, and large enterprises alike access to the kind of protection that used to be reserved for Fortune 500 companies.
-
Built-In Resilience
Unlike firewalls or antivirus programs that need frequent updates or software installations, DNS doesn’t require constant attention. When set up correctly, it silently blocks malicious queries, balances legitimate traffic, and routes users away from trouble spots—all without you lifting a finger.
Think of DNS as a digital traffic controller: redirecting, filtering, and optimizing every request made to your website. If a DDoS attack starts, your DNS system, if properly configured—acts as a barrier, soaking up the traffic and preventing it from ever reaching your server.
This built-in resilience gives your business time to respond while your site stays online. And because DNS is globally distributed by nature, it also ensures uptime and redundancy, even if one point of failure goes down.
-
Easy Maintenance
One of the biggest advantages of prioritizing DNS for DDoS defense is that it’s incredibly easy to manage and future-proof.
Whether you’re:
- Rebuilding your website
- Switching email providers
- Scaling your app to serve a national or international audience
Your DNS setup remains consistent and reliable. You don’t need to reconfigure your entire infrastructure every time you grow or upgrade. You simply adjust DNS settings—something you can do from your telaHosting dashboard in minutes.
This flexibility makes DNS an ideal solution for growing businesses. You’re not locked into one tool or system. As your brand evolves, your DNS defenses grow with you, ensuring long-term security with minimal fuss.
-
Boosts Brand Reliability
In Nigeria’s competitive digital landscape, online trust is everything. A single hour of downtime can damage your brand reputation, make customers question your professionalism, and even drive them straight to your competitors.
DDoS attacks don’t just knock your website offline—they knock your credibility offline.
Here’s what happens when DNS is prioritized:
- Your site stays online during an attack because DNS filters and absorbs most of the fake traffic.
- Your customers enjoy uninterrupted service, even when attackers try to bring you down.
- Your business builds a reputation for reliability—a powerful advantage in sectors like fintech, e-commerce, education, and healthcare where trust matters most.
At telaHosting, we’ve seen this firsthand: clients who invest in DNS-based protection bounce back faster, lose less, and gain more in customer confidence compared to those who don’t.
Step-by-Step Checklist: Fortify DNS Against DDoS Attacks
Use this guide to audit or build your protection:
- Use Anycast DNS with multiple point-of-presence
- Configure geo-load balance rules
- Enable anomalous traffic detection and challenge-response
- Block/blacklist malicious IP addresses
- Explore scrubbing services or secondary DNS providers
- Harden both DNS and application layers with rate-limiting
- Set longer TTL values on stable records
- Turn on DNSSEC
- Test with DDoS simulations
- Monitor performance and maintain so you stay ahead
How telaHosting Equips Your Business for DNS-Based DDoS Defense
Here’s how we help Nigerian entrepreneurs and enterprises build rock-solid protection:
- Globally distributed anycast DNS: fast and resilient even during surges
- Real-time threat detection: 24/7 alerting and automated mitigation tools
- DNSSEC support: adds trust and integrity to your domain records
- Traffic scrubbing & IP filtering: layers of defense that separate real users from malicious bots
- Expert local support: no bots or delays—just fast, experienced engineers
Conclusion
DDoS attacks can knock any online business offline, but with smart DNS management, you’re not defenseless. DNS carries far greater power than simply pointing browsers—it’s a strategic pillar that shapes traffic flow, verifies trust, and fends off digital threats.
At telaHosting, we believe security starts before the threat reaches your servers. With built-in DNS-based DDoS defenses, our mission is to help Nigerian businesses stay online, trusted by users, and ready for growth.
Stay ahead. Digitally safe. Proudly Nigerian.
FAQs
- Can DNS alone fully stop a DDoS attack?
DNS is your first line, but not the whole solution. Layered defenses, scrubbing services, and backup DNS/CDN add protection. - Will Anycast DNS slow down my site in Nigeria?
No—Anycast improves speed because users connect to the nearest edge server, reducing latency. - How do I know if I’m under attack?
Watch for sudden traffic surges, website slowness, repeated connection errors, or alerts from your DNS monitoring. - Is DNSSEC necessary for DDoS protection?
It doesn’t block flooding, but it stops cache poisoning that could support a DDoS campaign. - Does telaHosting offer DDoS support for smaller teams?
Yes. We offer scalable options with no hidden fees—ideal if you run on a lean Nigerian team.